Thank you very much, perfect hint! Now it works within InstallAware as well. We'll now try to explain 1st how to create a certificate for testing purposes and 2nd what our problem was, just for the community:
We create a testing certificate:
Makecert.exe -a sha1 -b 01/01/2010 -e 01/01/2015 -in "CN=TestCert" -sv TestCert.pvk TestCert.cerAfter that we have to convert the certificate from CER to SPC:
Cert2spc.exe TestCert.cer TestCert.spcAfter that we do the code signing itself:
Signcode.exe -spc TestCert.spc -v TestCert.pvk "C:\InstallAware\Release\Setup.exe" -t "http://timestamp.verisign.com/scripts/timstamp.dll"This all works fine, the Setup.exe is code signed with our self created certificate, but the certificate is not fully valid because of it's "Root certificate" (keep in mind we are still using a testing certificate):
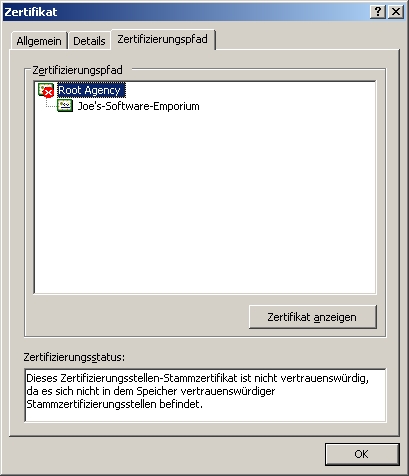
- TestCert01.jpg (50.25 KiB) Viewed 21383 times
As you see the root certificate from "Root Agency" is red which means that all certificates beneath are invalid as well, means our testing certificate from "Joe's-Software-Emporium" (name is given from Microsoft) is not valid at all.
Now, validating the Setup.exe whith
Signtool.exe verify -pa "C:\InstallAware\Release\Setup.exe"show's up an error pointing exactly this fact. So, what to do? We come closer ...
We have to put the root certificate from "Root Agency" into the proper certificate cache/path. Therefor we have to export the root certificate by clicking the button "Zertifikat anzeigen" / "Show certificate", then click somewhere the button "In Datei kopieren ..." / "Copy to file ..." and follow the steps of the wizard. After that doubleclick the file created and the click "Zertifikat installieren" / "Install certificate". That's all, that's it!
Now, validating the Setup.exe with
Signtool.exe verify -pa "C:\InstallAware\Release\Setup.exe"show's up NO ERROR. This certificate work's fine with InstallAware as well! That's it!